Indian Users Targeted in Tax Phishing Campaign Delivering Blackmoon Malware
https://firewalls.firm.in/wp-content/uploads/2026/01/itd.jpg

Cybersecurity researchers have discovered an ongoing campaign that’s targeting Indian users with a multi-stage backdoor as part of a suspected cyber espionage campaign.
The activity, per the eSentire Threat Response Unit (TRU), involves using phishing emails impersonating the Income Tax Department of India to trick victims into downloading a malicious archive, ultimately granting the threat actors persistent access to their machines for continuous monitoring and data exfiltration.
The end goal of the sophisticated attack is to deploy a variant of a known banking trojan called Blackmoon (aka KRBanker) and a legitimate enterprise tool called SyncFuture TSM (Terminal Security Management) that’s developed by Nanjing Zhongke Huasai Technology Co., Ltd, a Chinese company. The campaign has not been attributed to any known threat actor or group.

“While marketed as a legitimate enterprise tool, it is repurposed in this campaign as a powerful, all-in-one espionage framework,” eSentire said. “By deploying this system as their final payload, the threat actors establish resilient persistence and gain a rich feature set to monitor victim activity and centrally manage the theft of sensitive information.”
The ZIP file distributed through the fake tax penalty notices contains five different files, all of which are hidden except for an executable (“Inspection Document Review.exe”) that’s used to sideload a malicious DLL present in the archive. The DLL, for its part, implements checks to detect debugger-induced delays and contacts an external server to fetch the next-stage payload.
The downloaded shellcode then uses a COM-based technique to bypass the User Account Control (UAC) prompt to gain administrative privileges. It also modifies its own Process Environment Block (PEB) to masquerade as the legitimate Windows “explorer.exe” process to fly under the radar.
On top of that, it retrieves the next stage “180.exe” from the “eaxwwyr[.]cn” domain, a 32-bit Inno Setup installer that adjusts its behavior based on whether the Avast Free Antivirus process (“AvastUI.exe”) is running on the compromised host.
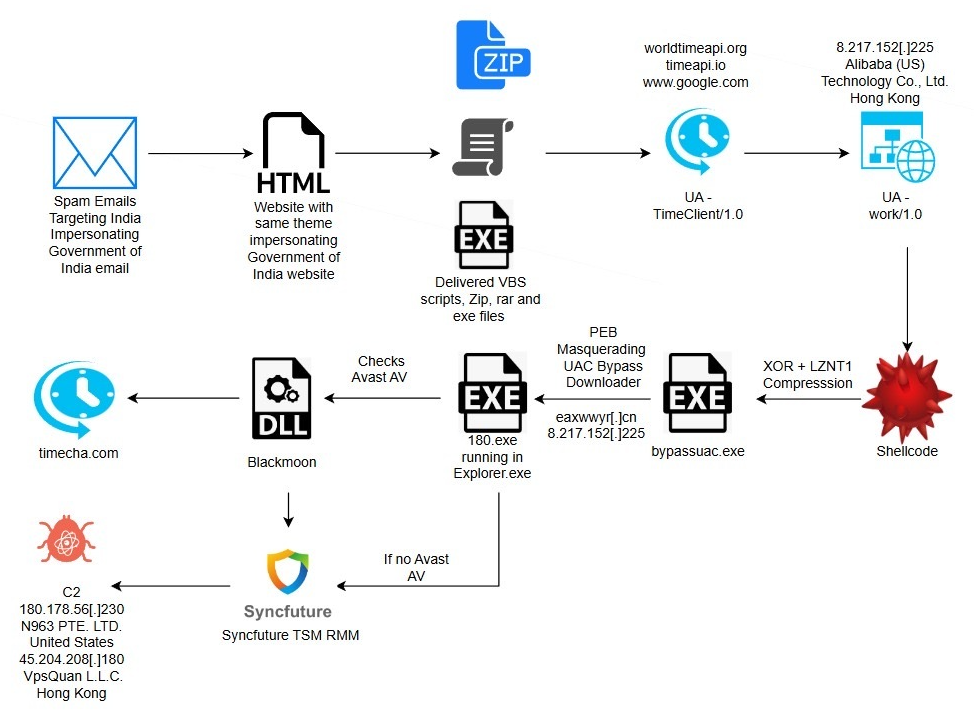
If the security program is detected, the malware uses automated mouse simulation to navigate Avast’s interface and add malicious files to its exclusion list without disabling the antivirus engine to bypass detection. This is achieved by means of a DLL that’s assessed to be a variant of the Blackmoon malware family, which is known for targeting businesses in South Korea, the U.S., and Canada. It first surfaced in September 2015.
The file added to the exclusion list is an executable named “Setup.exe,” which is a utility from SyncFutureTec Company Limited and is designed to write “mysetup.exe” to disk. The latter is assessed to be SyncFuture TSM, a commercial tool with remote monitoring and management (RMM) capabilities.

In abusing a legitimate offering, the threat actors behind the campaign gain the ability to remotely control infected endpoints, record user activities, and exfiltrate data of interest. Also deployed following the execution of the executable are other files –
- Batch scripts that create custom directories and modify their Access Control Lists (ACLs) to grant permissions to all users
- Batch scripts that manipulate user permissions on Desktop folders
- A batch script performs cleanup and restoration operations
- An executable called “MANC.exe” that orchestrates different services and enables extensive logging
“It provides them with the tools to not only steal data but to maintain granular control over the compromised environment, monitor user activity in real-time, and ensure their own persistence,” eSentire said. “By blending anti‑analysis, privilege escalation, DLL sideloading, commercial‑tool repurposing, and security‑software evasion, the threat actor demonstrates both capability and intent.”
 Firewall Security Company India Complete Firewall Security Solutions Provider Company in India
Firewall Security Company India Complete Firewall Security Solutions Provider Company in India











