The Future of Security in 2026, ETCISO Organizations’ perspectives on security are rapidly changing. Building robust barriers and hoping that attackers stayed out were the main approaches to security a few years ago. Today, however, people work remotely, threats move too rapidly and applications are spread across cloud, data centre and edge locations. The outdated “trust but verify” approach just ...
Read More »Blog
Microsoft, Meta, Google and Apple warned over AI outputs by US attorneys general
Microsoft, Meta, Google and Apple warned over AI outputs by US attorneys general https://etimg.etb2bimg.com/thumb/msid-125902911,imgsize-24128,width-1200,height=627,overlay-etciso,resizemode-75/data-breaches/us-attorneys-general-warn-tech-giants-like-microsoft-and-apple-over-ai-risks.jpg Microsoft, Meta, Google and Apple were among the 13 companies that received a warning from a bipartisan group of state attorneys general, according to a letter from the state leaders, who said their chatbots’ “delusional outputs” could be violating state laws. The letter was made public ...
Read More »Cybercriminals Abuse Google Cloud Email Feature in Multi-Stage Phishing Campaign
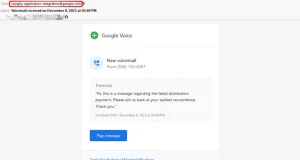
Cybercriminals Abuse Google Cloud Email Feature in Multi-Stage Phishing Campaign https://firewalls.firm.in/wp-content/uploads/2026/01/phishing-email.jpg Jan 02, 2026Ravie LakshmananCloud Security / Email Security Cybersecurity researchers have disclosed details of a phishing campaign that involves the attackers impersonating legitimate Google-generated messages by abusing Google Cloud’s Application Integration service to distribute emails. The activity, Check Point said, takes advantage of the trust associated with Google Cloud ...
Read More »European Space Agency confirms cyberattack on some its systems
European Space Agency confirms cyberattack on some its systems https://etimg.etb2bimg.com/thumb/msid-126298138,imgsize-105962,width-1200,height=627,overlay-etciso,resizemode-75/data-breaches/european-space-agency-confirms-cyberattack-on-some-its-systems.jpg The European Space Agency (ESA) has confirmed a cyberattack on some of its systems after a hacker offered to sell data allegedly stolen from the organisation. The agency’s forensic investigation has revealed that servers located outside the ESA corporate network have been compromised. According to ESA, only a very small ...
Read More »Policy debate or execution challenge?, ETCISO
Policy debate or execution challenge?, ETCISO For any Indian enterprise, the latest set of policy directives around DPDP is akin to a hard reset. It’s a bold set of reforms with reports indicating an escalation in compliance costs – some indicating a 15% rise in operational expenses for advertising agencies. In comparison, another estimate predicts a 30% jump in compliance ...
Read More »Global cyberattacks rise as GenAI introduces new data exposure risks: CPR November 2025 findings
Global cyberattacks rise as GenAI introduces new data exposure risks: CPR November 2025 findings https://etimg.etb2bimg.com/thumb/msid-125909289,imgsize-149288,width-1200,height=627,overlay-etciso,resizemode-75/data-breaches/surge-in-global-cyberattacks-genai-data-exposure-risks-highlighted-by-cpr-november-2025-report.jpg Check Point Research, the threat intelligence arm of Check Point Software Technologies, released its Global Threat Intelligence insights for November 2025, reporting that organizations worldwide faced an average of 2,003 cyberattacks per week. This reflects a 3% increase from October and a 4% rise year-over-year, ...
Read More »New MongoDB Flaw Lets Unauthenticated Attackers Read Uninitialized Memory
New MongoDB Flaw Lets Unauthenticated Attackers Read Uninitialized Memory https://firewalls.firm.in/wp-content/uploads/2025/12/mongodb.jpg Dec 27, 2025Ravie LakshmananDatabase Security / Vulnerability A high-severity security flaw has been disclosed in MongoDB that could allow unauthenticated users to read uninitialized heap memory. The vulnerability, tracked as CVE-2025-14847 (CVSS score: 8.7), has been described as a case of improper handling of length parameter inconsistency, which arises when ...
Read More »The year the cloud went dark: Inside 2025’s biggest tech outages
The year the cloud went dark: Inside 2025’s biggest tech outages https://etimg.etb2bimg.com/thumb/msid-126199542,imgsize-2412700,width-1200,height=627,overlay-etciso,resizemode-75/cybercrime-fraud/the-year-the-cloud-went-dark-inside-2025s-biggest-tech-outages.jpg The year 2025 highlighted the internet’s vulnerability. Major cloud providers like AWS, Microsoft Azure, and Google Cloud experienced significant outages. For a world that lives online, 2025 was a reminder of just how fragile the internet’s backbone can be. From payment systems and airlines to messaging apps and ...
Read More »A Growing Threat to Digital Security, ETCISO
A Growing Threat to Digital Security, ETCISO Amid a rise in Telegram-based scams affecting users across India, cybersecurity researchers have identified several concerning patterns. Fraud actors are increasingly using the platform’s encrypted channels to circulate fake investment opportunities, lottery claims, and job offers. These schemes often lead to financial losses, identity theft, and malware infections through phishing links and malicious ...
Read More »BFSI leaders decode how privacy is becoming a competitive edge
BFSI leaders decode how privacy is becoming a competitive edge https://etimg.etb2bimg.com/thumb/msid-125931099,imgsize-88480,width-1200,height=627,overlay-etciso,resizemode-75/data-breaches/bfsi-leaders-reveal-privacy-as-new-competitive-advantage-in-data-protection.jpg At the ETCISO Data Protection & Privacy Summit 2025, senior leaders from Bandhan Bank and Star Health & Allied Insurance unpacked how India’s new data protection regime is triggering a decisive shift — from viewing privacy as a compliance formality to positioning it as a strategic asset. The discussion ...
Read More » Firewall Security Company India Complete Firewall Security Solutions Provider Company in India
Firewall Security Company India Complete Firewall Security Solutions Provider Company in India